IoT Security: Could Careless Talk Cost Livelihoods?
The rise of the Internet of Things (IoT) promises exciting capabilities for business but could it usher in risks that are difficult to assess, let alone deal with? In a world where companies can use Alexa to help set up new office IT, could unsecured IoT systems be the equivalent of careless talk giving away company secrets – and endangering livelihoods?
But if IoT systems – and the teams developing them – aren’t brought into an overarching data and network security strategy, these technologies could become a weak link in big companies’ defences.
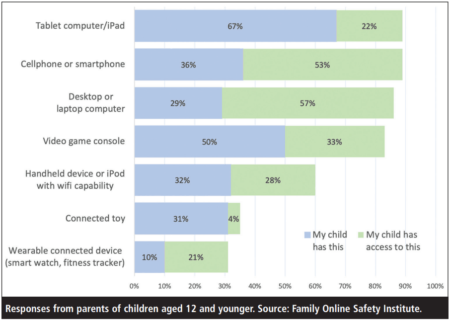
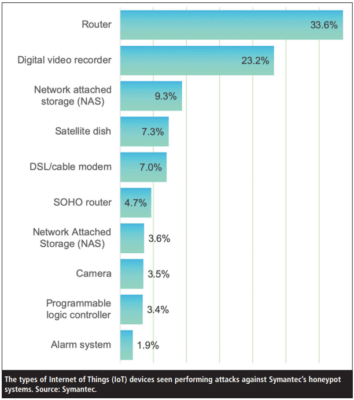
Demand for IoT is skyrocketing: Gartner forecasted that worldwide IoT spending would hit $1.5bn in 2018, up 28% on 2017. But risks are growing too: Symantec reported a 600% increase in IoT device attacks in 2017 (1) while the US Family Online Safety Institute’s research found that three in 10 parents had children potentially using Internet-enabled toys that share data (2): the potential for privacy breaches from poorly secured IoT products is huge.
The nub of these problems is that IoT-enabled devices behind cutting-edge consumer and business products must talk securely to the company’s core IT and business systems. Without this ‘secure conversation’, IoT’s learning capabilities could simply enable hackers to carry out wider-scale attacks. The problem is only exacerbated by companies’ complex network infrastructures and surging data volumes in our online world.
Planning IoT Security
Given this bewildering picture, how should in-house operational, network infrastructure and data security teams mitigate IoT risks? Can in-house personnel realistically run expanded security and network monitoring models? For all these reasons, IoT security presents a formidable challenge.
Addressing IoT system risks and dealing with them depends on companies developing regular risk analysis; bringing internal and external teams into IoT security planning; operating companywide security policies; protecting network endpoints and segmenting networks; generally achieving far better awareness of what is going on in their corporate IT networks; and engineering enhanced network control and automation in the future.
Assessing The Risk
Securing IoT means making a step change in understanding how individual components communicate with back-end IT systems and getting sufficient network visibility to plan better risk mitigation and security policies.
Another factor is commercial pressure on companies to cut process costs and speed up time to market. It’s likely that under-pressure in-house IT and security teams have quietly tried to fix security after a product’s launch. Organisations must stay one step ahead of consumers and potential attackers to safely develop next-stage products and services – without their products or reputation being compromised.
The risks from failing to bring IoT into the corporate security strategy are becoming clear. In a recent test, a children’s toy could be hacked and used to track children’s movements and listen remotely. Incidents like this could potentially sink a brand’s reputation or lead to consequential losses from lawsuits.
IoT security and the advanced analytics required have to be embedded in a company’s new product development (NPD) – and be robust enough to withstand commercial pressures and potential threats – from the start. These solutions must also be integrated with that under-realised challenge – getting a grip on today’s complex global networking infrastructures.
Organising network security, especially analysing the data generated to help evolve security policies, is a big task given the explosion in networks and cloud services. Company WANs not only reach from enterprises to the cloud but also across cloud regions and different vendors.
Increased mobile working also means more branch office and individual endpoint connections. And ever-wider connectivity options – such as MPLS, public Internet, 4G and 5G – also have to be managed for optimum performance and security.
With business data increasingly moving to the cloud, innovative companies will need fresh network insights if they are to fully grasp how their IoT systems communicate across the cloud and see how their security can be hardened.
In-depth Security
The overall task for global companies running global networks and cloud operations is naturally to defend in depth – based on network segmentation, employee access controls, reducing or controlling the level of remote access, strong password policies, use of encryption and separating sensitive networks and using trusted and audited third-party contractors.
But the real difference in effective security is being made in the crucial second part of the security task. This is when all that data arrives at the back end and IT teams try to understand whether hackers or criminals are piggybacking on that traffic – using logs, packet capture and meta traffic – to access core business or IoT systems.
But this second stage inevitably creates monitoring and analytics workloads that are often beyond the capabilities – and the budgets – of many internal IT and networking teams. And as savvy enterprise IT teams demand more visibility of data and network traffic to assist this task, it’s third-party networking and analytics experts that are giving corporate customers
the extra resources and new insights to cope with this workload.
Specialists will find gaps in the customer’s networks and IoT set-up and identify solutions to harden the security all the way to the data centre or the cloud: they give in-house teams the tools to get the IoT security job done.
As a result, we are already seeing global companies partnering with security vendors to protect IoT developments in their industrial platforms. There are readily available tools such as open source network traffic analysers being used for live event monitoring or as flexible analytical platforms for network performance measurement and troubleshooting.
These innovations give hard-pressed internal teams new options such as smarter post-processing or the use of alternative back-ends such as external databases for making added security checks.
As levels of incoming system and security data only increase, IT and security teams can bring in the people and systems to segment traffic and the corporate network fabric to ensure that the right data goes to the right place. As a result, corporate IT and security gain fuller visibility of traffic, events and suspicious behaviour on core and IoT networks and devices to feed into their security plans.
Enforcing Policies
Companies are highly motivated with regards to security following high-profile hacks and the arrival of the General Data Protection Regulation (GDPR). But a lasting barrier to locking down IoT is the lack of understanding and co-operation between internal NPD, IT and security teams.
As IoT is widely adopted, organisations need closer co-operation between operational technology professionals (dealing with IoT devices as part of NPD) and IT and infrastructure
teams (handling network infrastructure monitoring and optimisation) and security teams driving overall strategy and enforcement. Ad hoc thinking, such as NPD plugging gaps revealed by penetration tests, has to give way to co-ordinated company-wide policies.
While internal collaboration is improving, companies need to organise wider education and training on responsibilities for all internal teams, taking account of business goals, corporate and IoT security needs, desired solutions and analytics resourcing plans. IoT security demands that everyone pulls in the same direction.
Network Segmentation
It’s fundamental to securing IoT that enterprise networks and devices should not meet, since this creates many opportunities for unauthorised access of core networks using sensors and devices. Working with outside experts in network traffic segmentation, IT teams can define relevant controls, so that only desired traffic passes between systems or traffic takes only defined paths between zones.
In-house teams that enlist external specialists can better assess their networking landscapes and desired traffic flows and draw up enhanced segmentation policies. As well as supporting IoT security planning, this joint approach also reduces companies’ industry and legal compliance workloads.
Anticipating Risks
Global businesses will always need to continually review their security posture and policies and drive enforcement. Can any IT or security team ever say that they have done enough without asking for outside help or more budget?
For example, a business services company that has implemented firewalls and enabled endpoint security may struggle with the details of segmentation before it can take steps to achieving better IoT protection. There is a broad comparison with GDPR here: companies cannot develop perfect solutions but they can take practical steps and selectively use outside specialists to help ensure workable security systems.
And looking ahead, how do enterprises investing heavily in NPD and IoT strategies simplify their security planning? An important opportunity is coming with the growing use of software-defined wide area networks (SD-WAN) to put control layers over companies’ different networks and components.
This advance will bring benefits like IT teams better controlling WANs from a central point, clearer pictures of network issues and intelligent routing of traffic across networks. SD-WAN could enable companies to re-architect legacy networks and potentially gain greater insights into business applications and potential threats to them as the backdrop to long-term IoT development.
Companies excited by IoT’s real-time capabilities need to ensure that their security is ‘next-generation’ too. While investing in IoT innovations, enterprises need to enlist external analytics and security expertise to mitigate risks and realise their exciting commercial opportunity.
References
1. ‘Internet Security Threat Report: Volume 23’. Symantec. Accessed Apr 2019. www.symantec.com/content/dam/symantec/docs/reports/istr-23-2018-en.pdf.
2. ‘Connected Families: how parents think & feel about wearables, toys, and the Internet of Things’. Family Online Safety Institute. Accessed Apr 2019. www.fosi.org/policy-research/connected-families/.
About The Author
Marc Sollars is VP of Business Development at Teneo, an expert Managed Service Provider. He is chief evangelist and plays a key role in identifying technologies that are early to market and can be integrated into the company’s services portfolio. Sollars is on Twitter at @MarcatTeneo.
This article was originally published in the May 2019 of Computer Fraud & Security. The full edition of the magazine can be found here.


