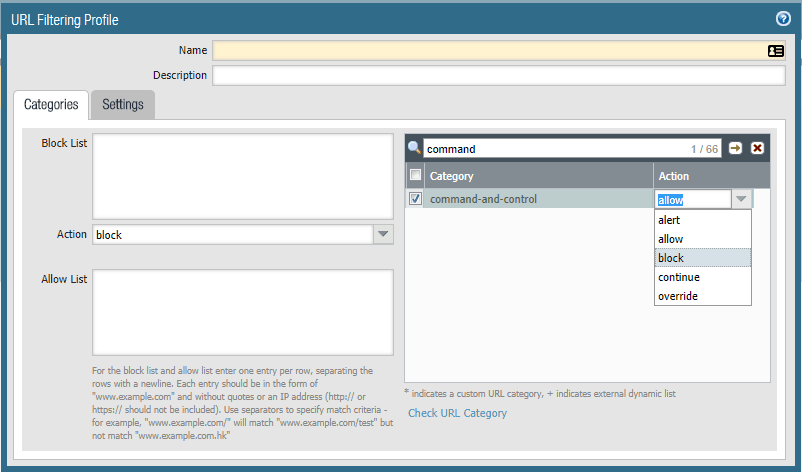
Palo Alto URL Filtering category: Command-and-control
Palo Alto Networks have added a new URL filtering category called ‘command-and-control’, to identify the differences between malware and command and control (c2) URLs and domains. Until the new category is live, the URLs and domains are recorded with the malware category.
Palo Alto quote ‘This command-and-control category is defined as command-and-control URLs and domains that are used by malware or compromised systems to surreptitiously communicate with an attacker’s remote server to receive malicious commands or to exfiltrate data.’
why does this matter?
This is an important distinction by Palo Alto because an endpoint contacting a c2 server has probably already been compromised, requiring remediation and possible lateral movement of the infection throughout the IT infrastructure.
Whereas an endpoint attempting to contact a malware URL is probably the victim of a phishing or drive-by-download and is yet to be infected/compromised.
Palo Alto Networks and Teneo highly recommend that administrators update the policy action for this new command-and-control category to BLOCK on all the URL Filtering policies across the PAN estate, see the screen capture below.
Teneo best practices recommend combing this new URL category with DNS Sinkholing, granular log forwarding with email alerts and custom reporting. In doing so, the internal IT support department will have near instant visibility of a comprised endpoint on the network and can take the appropriate action to isolate and remediate the endpoint.
Please contact us if you’d like our Professional Services team to help with configuring the firewalls, to follow our recommended best practices and gain that all important visibility into compromised endpoints.
Palo Alto Command-and-Control (C2) FAQ