Stop Viewing Cybersecurity as an Expense
Nine. Million. Dollars. Well, $9.44 million to be exact for your average data breach according to the latest report from IBM, Cost of a Data Breach Report 2022. From 2017 to 2022, that number has only continued increasing from $7.35 million, an almost 30% increase in just five years. For a small company, a security breach can be the difference between staying open or closing the business. And for a Fortune 500 enterprise, that cost will be more severe. For example, Marriott Hotels were fined £18.4 million ($23.98 million) in 2018 after their Starwood Hotels acquisition. They even came out lucky, as the fine was much lower from the initial proposed fine of £99.2 million ($129.28 million).
For the past few years, rightly so, cybersecurity has become a priority for many organizations, governments, and regulatory bodies. However, even with this increased focus, many organizations still view cybersecurity and IT as an expense. Just like with most expenses, companies would like to reduce costs. Simply put, this view cannot exist in the constantly changing landscape of IT and cyber security threats. Not only is this ever-evolving IT landscape a struggle for companies to keep up with, but even the security engineers and IT teams are struggling to implement and manage these new security philosophies and designs.
Recently, enterprises have been deploying Next Generation Firewalls (NGFWs) with all sorts of flashy and new ways to stop attacks. For some time, this was a great solution. Then COVID-19 happened… leading to a significant change in how employees interact and access their IT systems due to a sudden rise in hybrid working and cloud integrations. The idea of a perimeter around your network and infrastructure is long gone in today’s environment. Having NGFWs to always protect your network is not feasible. It is simply too expensive, difficult to implement, and when it is implemented after months, if not years, it is too difficult to manage and meet the ever-changing compliance requirements.
It’s not surprising that many people in IT, from the junior network engineer to the CIO, are pulling their hair out when dealing with these problems. The landscape and technologies are changing too fast for many to keep up to date with. Now, more than ever, it is important to have a technology partner, not just a vendor, that you can rely on to help you and your team to save time, money and reduce risk”
That’s why Teneo is proud to partner with Akamai, which tackles these new security issues head-on with Akamai Guardicore Segmentation, a modern and easy approach to resolve a modern and difficult problem. With the attack surface and perimeter expanding, Akamai addresses these concerns by implementing a microsegmentation approach.
So, what is microsegmentation? And don’t we already segment our networks?
Most likely, your organization is already segmenting its network via VLANs, subnetting, and some type of access control list or port-based security. But the problem with these methods lies in that very statement. Currently your organization is only able to segment your network based off of a VLAN, IP address, or a TCP/IP port. Let’s also not forget, managing and implementing these methods at even a moderate scale, is a next to impossible feat.
This is where microsegmentation comes into play. Instead of only being capable of segmenting your LAN up to Layer 4 traditionally, microsegmentation can extend that control all the way to Layer 7. With the use of Akamai Guardicore Segmentation, you can have even more granular control by going down to the process-level on each individual machine. Not just device, not just application, but down to the process level to give security teams complete control of their dataflows. The entire premise of microsegmentation revolves around providing that flexibility and control that today’s IT and security teams need. But how else can Akamai enhance this concept?
Akamai Guardicore Segmentation is not only built on the concept of microsegmentation, but also on the philosophy of recognizing what organizations and security teams are facing; opting in to provide and create an easy, simple, and effective solution for anyone to implement and manage.
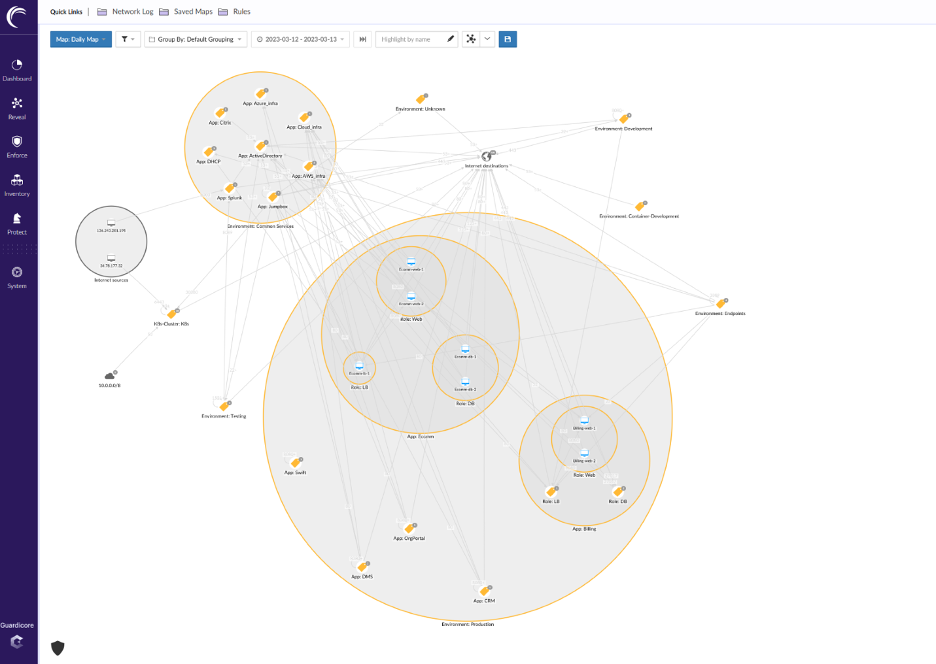
With network and process-level visibility into east-west traffic flows, security teams gain valuable insight into how their devices and applications communicate and interact with one another. Akamai Guardicore Segmentation then creates an interactive visual map based on labels that can be manually or automatically assigned to devices.
Due to the use of labels, infrastructure and applications are tied to these labels as opposed to an IP address. Thus, allowing your security team to create enforcement policies around labels, processes, or individual hostnames instead of worrying about IP address ranges or a device changing an IP address. To continue making the engineering team’s life easier, Akamai will also recommend policies utilizing machine learning based on how devices and processes communicate.
Akamai Guardicore Segmentation has a great GUI and tools to help security teams understand their network flows in order to create policies, but what happens when your organization suffers an attack? It’s a valid question, and not an if but a when. Since in 2022, 83% of organizations surveyed by IBM suffered one or more attacks.
Just like the rest of the platform, enforcement and security violations are designed to be easy to understand and quickly remediated. Utilizing the same type of map, Akamai gives your team a simple view into what the security violation is, as well as recommended actions to take that can let you swiftly isolate and contain any threat, leaving you with no worries or doubt if your network is still compromised or not.
Today, organizations and IT teams are in a never-ending battle where they need to be more agile and efficient than ever before. With that aspect in mind, Akamai Guardicore Segmentation rises to the occasion, prioritizing simplicity and providing the tools to empower its users. According to a Forrester report, this key design philosophy leads to an increase in security operations productivity by 95% which in turn, “from the increase in productivity… this time is redirected towards other projects and business needs.” With the clear understanding and presentation of your IT environment, as well as tools that accelerates and enables any engineer—regardless of their experience—to quickly create policies and solve incidents; it is no wonder why Akamai Guardicore is a leader in the microsegmentation space.
For more information about Akamai Guardicore Segmentation solution with Teneo, review the product solution brief or book a 30-minute introductory session to explore how Teneo can help minimize the impact of cyber attacks.
Author: Thomas Rogers, Technical Customer Success Consultant