Cyber Asset Management
Making the case
Cyber-attacks are escalating in both frequency and complexity, with global cybercrime costs projected to hit $10.5 trillion annually by 2025, according to Cybersecurity Ventures’ Official Annual Cybercrime Report’. This dramatic rise in cyber threats highlights the critical need for comprehensive, proactive cybersecurity measures to protect organizations from increasingly complex and costly attacks.
Modern organizations face a significant challenge in maintaining visibility and control over their cyber assets. Gartner’s 2024 report on Attack Surface Management reveals that only 17% of organizations can clearly identify and inventory a majority of their assets, highlighting widespread visibility challenges.
Teneo’s Cyber Asset Management simplifies, automates and streamlines these efforts by providing unified asset discovery, continuous monitoring, and on demand compliance management.

Take a modern approach to Cyber Asset Management
Teneo’s Cyber Asset Management solution delivers real-time visibility and control over all assets across your network. By leveraging advanced analytics and continuous monitoring, it ensures every device, application, and user is accounted for and secure—enhancing your security posture and operational efficiency.
Our approach

Key Benefits:
- Comprehensive Visibility: Full asset discovery for a complete security overview.
- Proactive Risk Management: Address vulnerabilities before they escalate.
- Automated Compliance: Simplify adherence to regulatory standards.
- Cost Efficiency: Reduce manual processes and optimize resources.
- Scalability: Adaptable to evolving business needs.
- Improved Decision-Making: Actionable insights via real-time dashboards.
- Enhanced Security Posture: Minimize gaps and strengthen defenses.
Teneo’s Cyber Hygiene Service
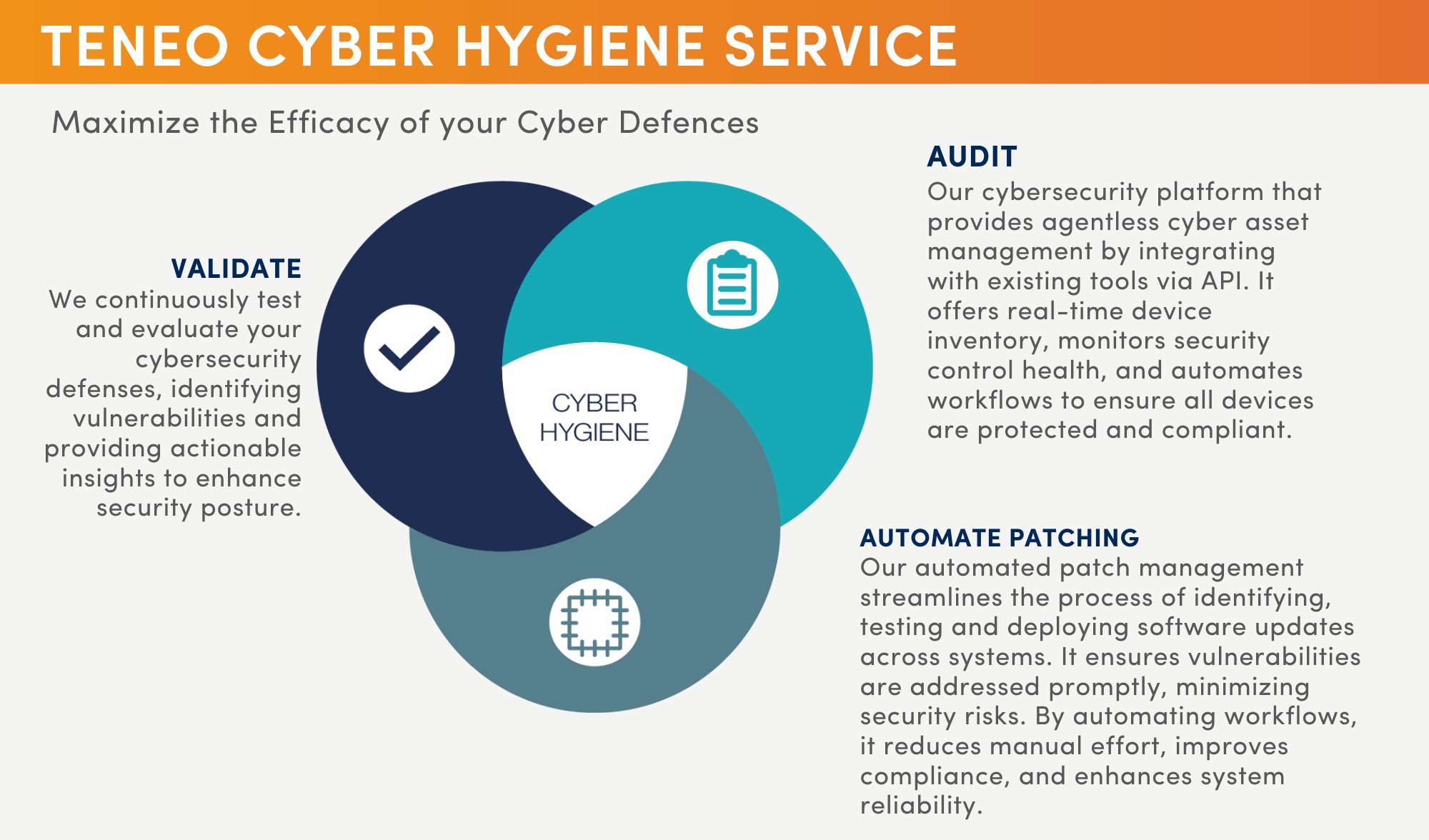
Cyber Asset Management is a core element of our Cyber Hygiene service, designed to help organizations optimize theeffectiveness of their cyber defenses. The diagram below illustrates the key elements of this service, with Cyber Asset Management playing a central role in the ‘Audit’ component.
StreamlineX
As part of Teneo’s StreamlineX framework, Cyber Asset Management enhances your organization’s security posture by providing comprehensive asset visibility, proactive risk mitigation, and automated compliance. This service integrates seamlessly with other StreamlineX solutions, ensuring holistic optimization and security across your digital ecosystem.
Schedule a conversation
To get started, simply schedule a conversation with us today.

